Placeholder blog post page 5
- Blog
- Placeholder blog post page 5
link here and here.
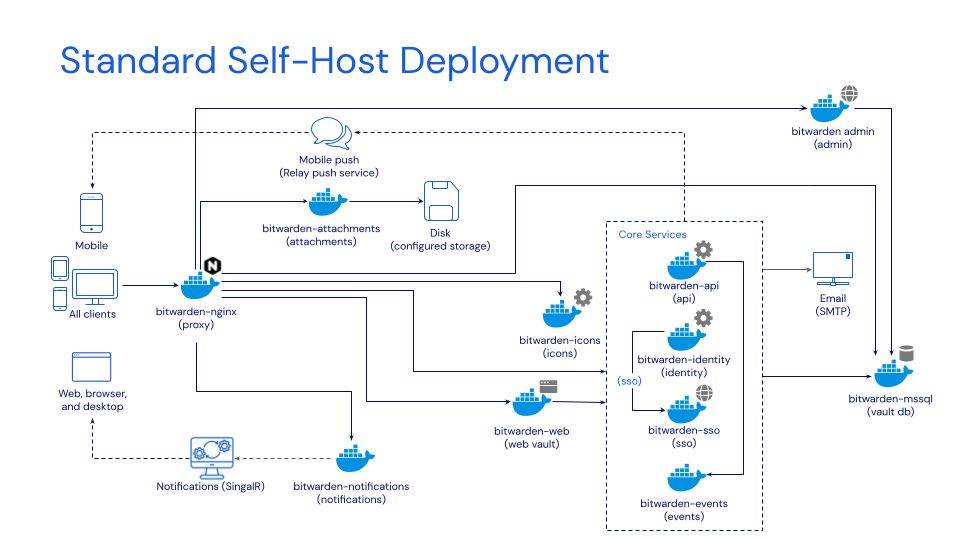
Password Management Maturity Model
Subtext
Status | Step | Level 2Launch | Level 3Evolve | Level 4Proactive | Level 5Leader |
|---|---|---|---|---|---|
Password Manager Deployment | Choose self hosted deployment method (Linux standard/manual/offline, Windows standard/offline, or Kubernetes) | Decentralized password management Ad hoc use of browser and other built-in password managers | Some centralized password management Stand-alone password manager rollout to one team | Rising employee adoption Company-wide stand-alone password manager rollout initiated | Complete organizational adoption Company-wide stand-alone password manager rollout complete Adoption enablement with mandatory use Offer family plans as employee benefit |
Security Culture | Minimal security awareness No emphasis on security best practices | Building on the basics Limited emphasis on security best practices | Security culture emerging Some security training available with limited accountability | Actionable employee awareness Security training program offered to the entire company with participation metrics | Employees leading security improvements Security training programs required for the entire company Clear channels where employees are encouraged to report suspicious activity |
Technical Maturity | Land of do-it-yourself Sensitive information often shared unencrypted | Isolated solutions Inconsistent approach to encrypted information Ad hoc use of 2FA | Coverage underway Cross-platform coverage across all devices Enables management of organizations and secure sharing between colleagues | Connected into IT workflows Directory Services integration Integrates with SSO | Comprehensive coverage and reporting Enables passwordless options from biometrics to passkeys Using APIs with automated scripting for integration with other tools, such as SIEM Mandatory 2FA |
Password Manager Deployment | Choose self hosted deployment method (Linux standard/manual/offline, Windows standard/offline, or Kubernetes) | Decentralized password management Ad hoc use of browser and other built-in password managers | Some centralized password management Stand-alone password manager rollout to one team | Rising employee adoption Company-wide stand-alone password manager rollout initiated | Complete organizational adoption Company-wide stand-alone password manager rollout complete Adoption enablement with mandatory use Offer family plans as employee benefit |



